
Executive Summary
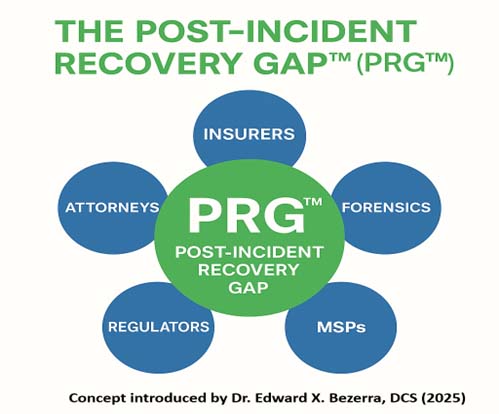
Cyber incidents generate immediate disruption, placing organizations at the intersection of insurers, breach counsel, forensic investigators, regulators, and internal IT teams. Each party plays a defined and necessary role, yet no single entity is responsible for overseeing the entire post-incident recovery lifecycle.
This structural vacuum is what we define as the Post-Incident Recovery Gap™ (PRG™). The PRG™ creates misalignment in coordination, inconsistent communication, conflicting evidence requirements, and extended uncertainty around when systems are truly ready for safe reconnection. As a result, organizations remain offline longer than necessary — not because remediation hasn’t occurred, but because no one is validating or certifying it.
As cyber insurers intensify scrutiny and supply chains become increasingly interconnected, independent recovery validation is emerging as a critical pillar of modern cyber resilience. This white paper explores the PRG™, its operational impact, and how objective validation shortens downtime, restores trust, and strengthens regulatory and insurer confidence.
What Is the Post-Incident Recovery Gap™? (PRG™)
The PRG™ refers to the absence of a single accountable party responsible for validating remediation and coordinating recovery after a cybersecurity incident. Every stakeholder focuses on their own scope — insurance on coverage, legal on documentation, forensics on root cause, and IT on restoration — but no one is tasked with certifying that the environment is truly ready for reconnection.
- Fragmented ownership and unclear decision authority
- Delayed validation of remediation activities
- Conflicting guidance from multiple stakeholders
- No unified recovery evidence package for insurers or regulators
- Customer and vendor reconnection delays
A Real-World Scenario
A mid-sized SaaS provider suffers a credential-based ransomware attack. Clients disconnect integrations immediately to protect their environments. While technical remediation progresses, reconnection is delayed — not due to risk, but due to insufficient cross-stakeholder evidence. Without independent validation, no party is confident enough to declare recovery complete. Days become weeks.
Benefits of Independent Recovery Validation
| Stakeholder | Core Concern | Outcome of Independent Validation |
|---|---|---|
| Insurers | Evidence of remediation accuracy | Clear, unified recovery package |
| Customers | Safety of reconnection | Faster, trusted reconnection |
| Breach Counsel | Regulatory defensibility | Documented forensic-proof evidence |
| Internal IT | Operational restoration | Objective validation of remediation steps |
Conclusion
The PRG™ exposes organizations to unnecessary downtime, financial impact, and erosion of customer confidence. Independent validation closes this gap by aligning stakeholders, certifying remediation, and establishing a defensible basis for full operational recovery.
To learn how CertiVend helps shorten recovery timelines and restore trust with objective post-incident validation, explore the full white paper below.